Roles
Administrators use roles to provide access to reporting content, themes and data-source servers in an efficient manner.
A role is either a collection of application users (that is, users added into the system already) and/or security groups as defined in the operating system's security framework (either the local users and groups or an Active Directory).
A role can include a combination of both user and groups, however, group security within a role will only provide group-wide access to existing application users.
Adding a Role
There are two ways to add roles: (1) individually or (2) multiples at a time through a preformatted document upload.
Adding roles individually
- Click the plus sign to add a New Role
- Enter a meaningful name for this role.
- Select whether the role is hidden. For explanation of a hidden role, click here.
- Click Next.
- Now add the users and/or groups to this role definition. Note that you must add at least one user or one security group to save the definition:
- Optionally add application users to this role definition. Users will be listed in the right hand panel. To retrieve a listing, use the find function in the top right hand corner of the dialog box. Select the users you wish to add to the role, and click the ADD button. Click Next.
- Optionally add security groups to this role definition. Groups will be listed in the right hand panel. To retrieve a listing, use the find function in the top right hand corner of the dialog box. Select the groups you wish to add to the role, and click the ADD button.
- Click Finish to commit your changes.
Once you have added a role, you can use it to apply data-source server access in the Servers Tab. Similarly, you can go to the User tab, select a user and then apply relevant roles to that user's definition.
Adding multiples roles at a time through file upload
- Administrators should go to the "Roles" tab and click on the "import" button (indicated with the red arrow).
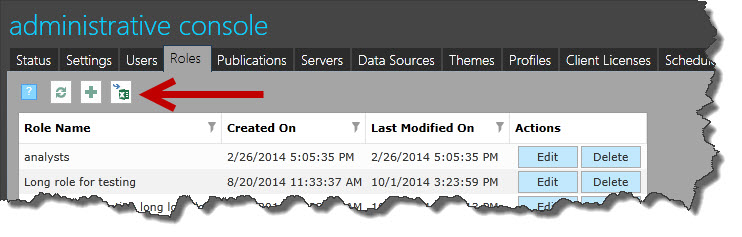
2. Click on the “Download Template” button and save the file on your computer.
3. Once the file has been downloaded, the template should be filled out as described below:
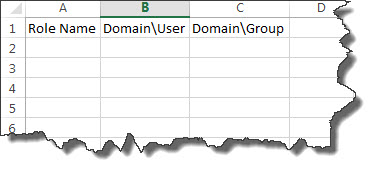
-
Role Name – a unique name is required.
-
Domain\User – a list of users that you want to add to this role definition. Both the domain and user name should be specific.
- Insert \ as a separator between the domain and the user.
- Insert a semicolon as a separator between users (for example: DEV\USER1:DEV\USER2).
-
Domain\Group – a list of group names that you want to add to this role definition. Both the domain and group should be specific.
- Insert \ as a separator between the domain and the group.
- Insert a semicolon as a separator between groups (for example: DEV\GROUP1:DEV\GROUP2).
4. Save the file as a comma delimited file.
5. Click on the "Upload File" button and browse to the correct file.
6.The system will process and validate the input. A status for each entry will be displayed
- Green – successful
- Red – failed
7. Click "Commit Successful Roles" to add the roles.
Hidden Roles
The administrator can choose to make a role 'hidden' - which means that this role can only be set or changed in the admin console. Users will not be able to view or change the role through the client application.
Editing a Role
Editing a role provides a very similar interface to the Add role functionality as described above.
- Click the EDIT button for the role you wish to edit.
- If required, change the role's name and/or whether the role is now "hidden". Click Next.
- Optionally, add or remove users that are associated with this role. Click Next.
- Optionally, add or remove security groups that are associated with this role.
- Optionally, add or remove users that are associated with this role. Click Next.
- Click Finish.
Deleting a Role
Administrators can delete a role by clicking its DELETE button.
Data Source Control
For a data source to be accessible to end users, it must be assigned roles. And users, in turn, must be assigned to these roles. This functionality adds another layer of data access control over and above (and in conjunction) with the data security provided by the cube servers.
Home |
Table of Contents |
Index |
User Community
Pyramid Analytics © 2011-2022

