Security
Security Overview
The application, content and underlying data is secured through a variety of measures:
Content Security
The Application's content management system (CMS) reflects a comprehensive and sophisticated security model for guarding access to content - over and above the security of the data (through the cube) or security of the functionality (through license type). Security is available at both the folder and book/dashboard level through a roles based model.
Security Roles are defined in the administrative console by system administrators. These roles are used primarily to manage access to items and their contents (reports/slides). Roles are used to a lesser extent to control access to data sources (see data security below).
Functional Security
Functional security is driven by the type of client license allocated to a user and any extended security profiles attached to a specific content item for a given role.. Their primary purpose is to differentiate between simplified and advanced functionality and publishing capabilities.
There are 4 types of licenses with 4 different levels of functionality:
- Viewer licenses - this client license allows users to access the viewer application only and consume predefined content available in the public folder domain only.They have limited interactive capabilities and cannot create or save any content for themselves or others.
- Consumer Licenses - this client license allows users to access to the application and consume predefined books or dashboards. However, they cannot start a new Data Discovery report from scratch and have some of the advanced choices in the client application limited. They are also presented with a different workspace (animated "viewer" by default).Most importantly, consumers CAN ONLY save content to the private domain and CANNOT see any content in the group domain (regardless of their security roles).
- Analyst Licenses - this client license type allows a user to access the entire application and consume predefined books or dashboards. This includes the ability to start new Data Discovery reports from scratch and to access all advanced functions. However, they CANNOT save content into the public domain.
- Professional Licenses - this client license type allows user to access the entire application and consume predefined books or dashboards. This includes the ability to start Data Discovery new reports from scratch and to access all advanced functions. Professional users can also save content to the private, group and public domains.
Independent of the functional security within the client application, users can be delegated administrative roles in the administrative tools:
- Full Administrator: have complete control of the application
- System Administrator - have the ability to set and maintain the "system" requirements of the application
- User Administrator - have the ability to create, edit and delete users and their security roles
See the Administrative Help Guide for more.
Data Security
Data security is driven effectively by the security roles defined within the cubes themselves by the cube administrators. The application facilitates this data security layer by accessing the cubes as the user - and in effect provides the SECURE mechanism for users to only interact with the cubes metadata and the query results. The details of data security can be found in third party manuals on Analysis Services Security Roles.
NOTE: In addition to the data security layer offered inherently in the cubes, the client Pyramid application blocks native access to the cube servers via the application UNLESS administrators have given users explicit access to the data source from within the administrative console.
Content Security Model
All users must belong to at least 1 role, as defined in the application's administrative console. This role framework is used primarily to govern access to content saved to the CMS. The logic for content access is illustrated and described below.
Content Domains
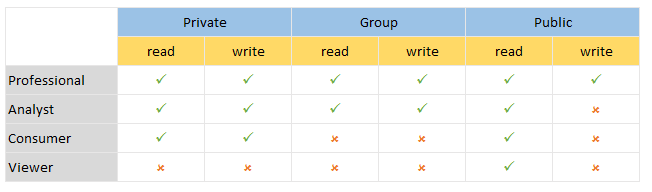
There are 4 content domains - Private, Group, Public and Legacy. Access to these domains is controlled by the user's account, their roles and user's license type:
- Consumers, Analysts and Professional users have a private domain where they can read and write "my" books or dashboards controlled by their user account (not roles). No other user (except for administrators) has access to another user's private domain.
- Only analysts and professional users have read and write access to the group domain, but specific access to folders, books and dashboards within this domain is governed by role security.
- All users have read access to the public domain, but specific access to folders, books or dashboards within this domain is governed by role security. Only professional users can save content into the public domain
- Legacy content is read accessible by all user types. Content cannot be saved to the legacy domain by any user type.
Folders
Content can be organized into hierarchical folders within each domain. In turn, each folder can be secured with read/write permissions by role. When a user saves content to the CMS they can elect which roles will have read and write access to the folder and its sub-ordinate contents.
Books, Story Boards and Publications
When an item is saved into one of the domains and/or book folders, it can be secured with read/write permissions by role (which is independent of the folder it is saved into). However, an item will not be accessible to an end user if they do not at least have read access to its parent folder (and so on up the folder hierarchy tree).
Reports
Reports and report folders in a given book effectively inherit the security of the book; as do the slides in a dashboard. There is no way to set specific security settings for each item within a book or dashboard.
NOTE: Administrators with access to the content store can change any and all security settings from within the administrative console.
Extended Security
Extended Security Profiles, as described above, are used by content publishers to lock down the application for specific users (via roles) for a given content item. Providing more granular control of the application, extended security provides a quick and elegant solution to both content and data access through the lock down of certain advanced analytic functions. See Extended Security for more.
Home |
Table of Contents |
Index |
User Community
Pyramid Analytics © 2011-2022

